DigiNotar, the Dutch certificate authority was recently the center of a significant hacking case. On the 19th July, the CA discovered that at least 531 rogue certificates has been issued. However, it was only in August that the attacked became public knowledge.
Security firm, Fox-IT were hired to investigate the breach, and the compromise has incurred financial losses that have caused the DigiNotar to declare bankruptcy.
So what happened? Fox-IT reported to net-security.org:
“The most critical servers contain malicious software that can normally be detected by anti-virus software,” it says. “The separation of critical components was not functioning or was not in place. We have strong indications that the CA-servers, although physically very securely placed in a tempest proof environment, were accessible over the network from the management LAN.”
All CA servers were members of one Windows domain and all accessible with one user/password combination. Moreover, the used password was simple and susceptible to brute-force attacks.
The software installed on public-facing web servers was outdated and unpatched, and no antivirus solution was installed on them. There was no secure central network logging in place, and even though the IPS was operational, it is unknown why it didn’t block at least some of the attacks.
The DigiNotar-controlled intermediates have been blacklisted in Mozilla Firefox and Google Chrome, and also by other browser manufacturers. The Dutch government announced on September 3, 2011, that they will switch to a different firm as certificate authority.
Some of the certificates signed by Diginotar include *.google.com, and even attempted signing certificates for double-wildcarded certificates for *.*.com and *.*.org. There seems to be some confusion whether these “double wildcard” certificates are valid but if they are then no DigiNotar-protected .com or .org sites could be trusted.
In the last week, The Register has reported researchers have discovered a serious weakness in virtually all websites protected by the secure sockets layer protocol that allows attackers to silently decrypt data that’s passing between a webserver and an end-user browser.
If true, the underlying vulnerability is present in virtually all applications that use TLS 1.0, making it possible to apply the technique to instant messenger and Virtual Private Networking programs.
Although TLS 1.1 has been available since 2006 and isn’t susceptible, virtually all SSL connections rely on the vulnerable TLS 1.0, as The Register reports;
“While both Mozilla and the volunteers maintaining OpenSSL have yet to implement TLS 1.2 at all, Microsoft has performed only slightly better. Secure TLS versions are available in its Internet Explorer browser and IIS webserver, but not by default. Opera remains the only browser that deploys TLS 1.2 by default.”
As also reported by The Register; this handy image explains all;
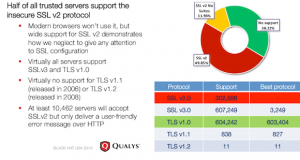
As reported; “What prevents people is that there are too many websites and browsers out there that support only SSL 3.0 and TLS 1.0. If somebody switches his websites completely over to 1.1 or 1.2, he loses a significant part of his customers and vice versa.”

